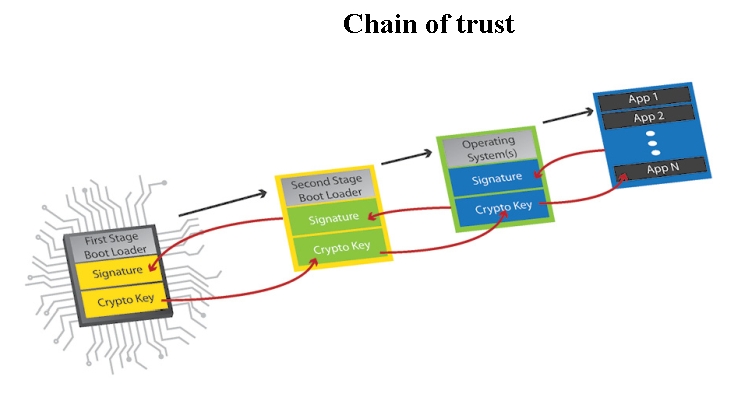
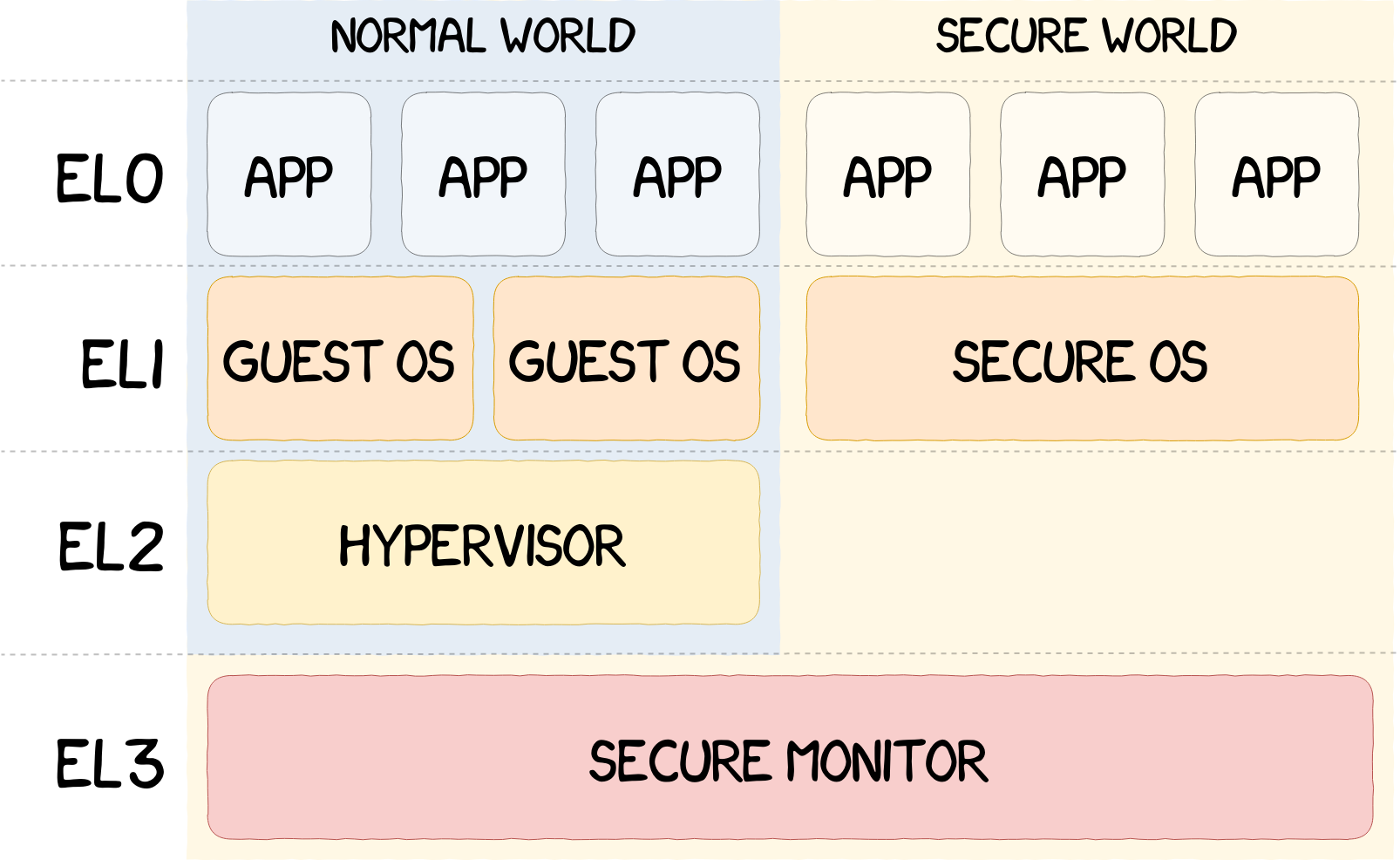
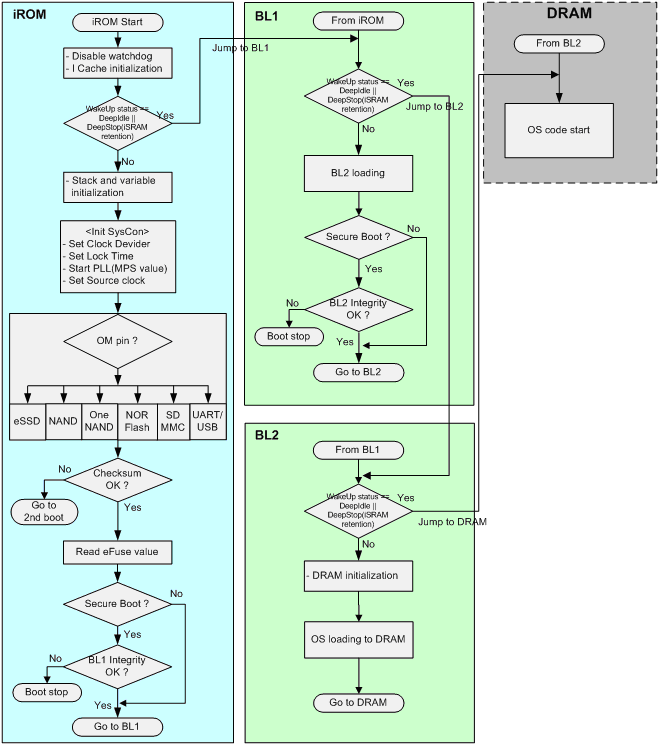
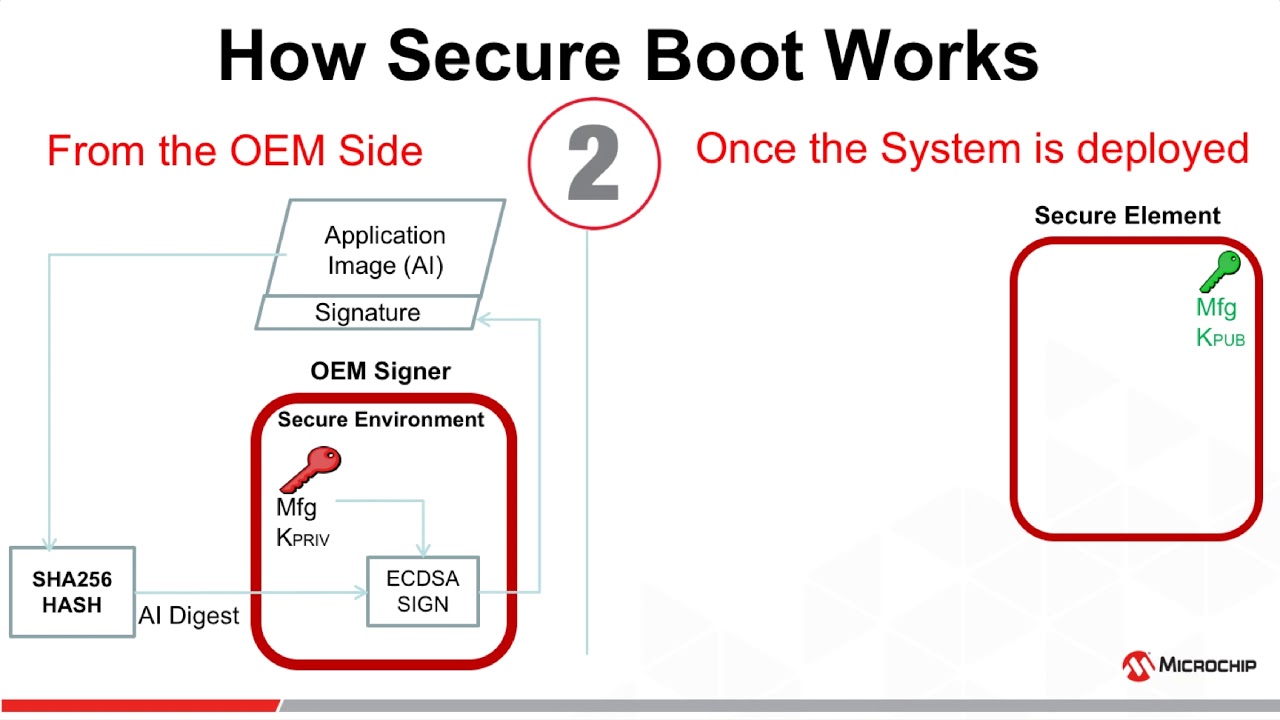
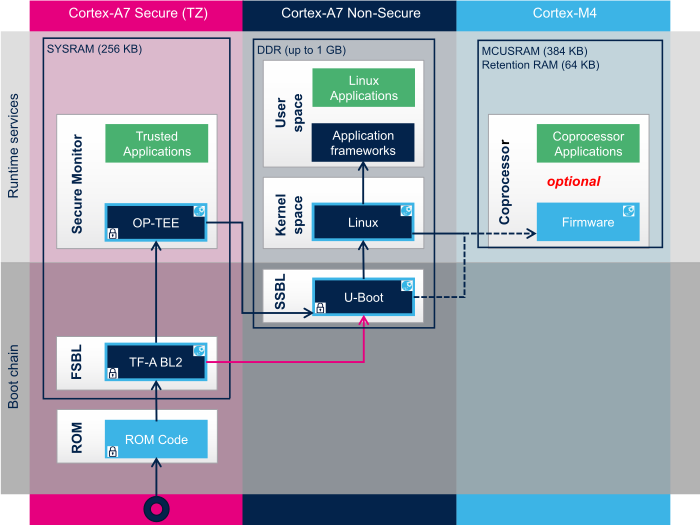
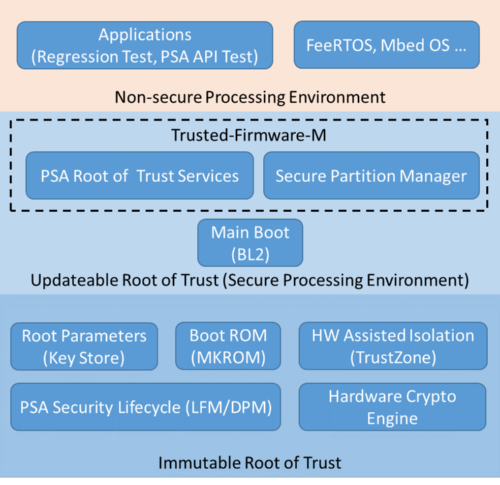
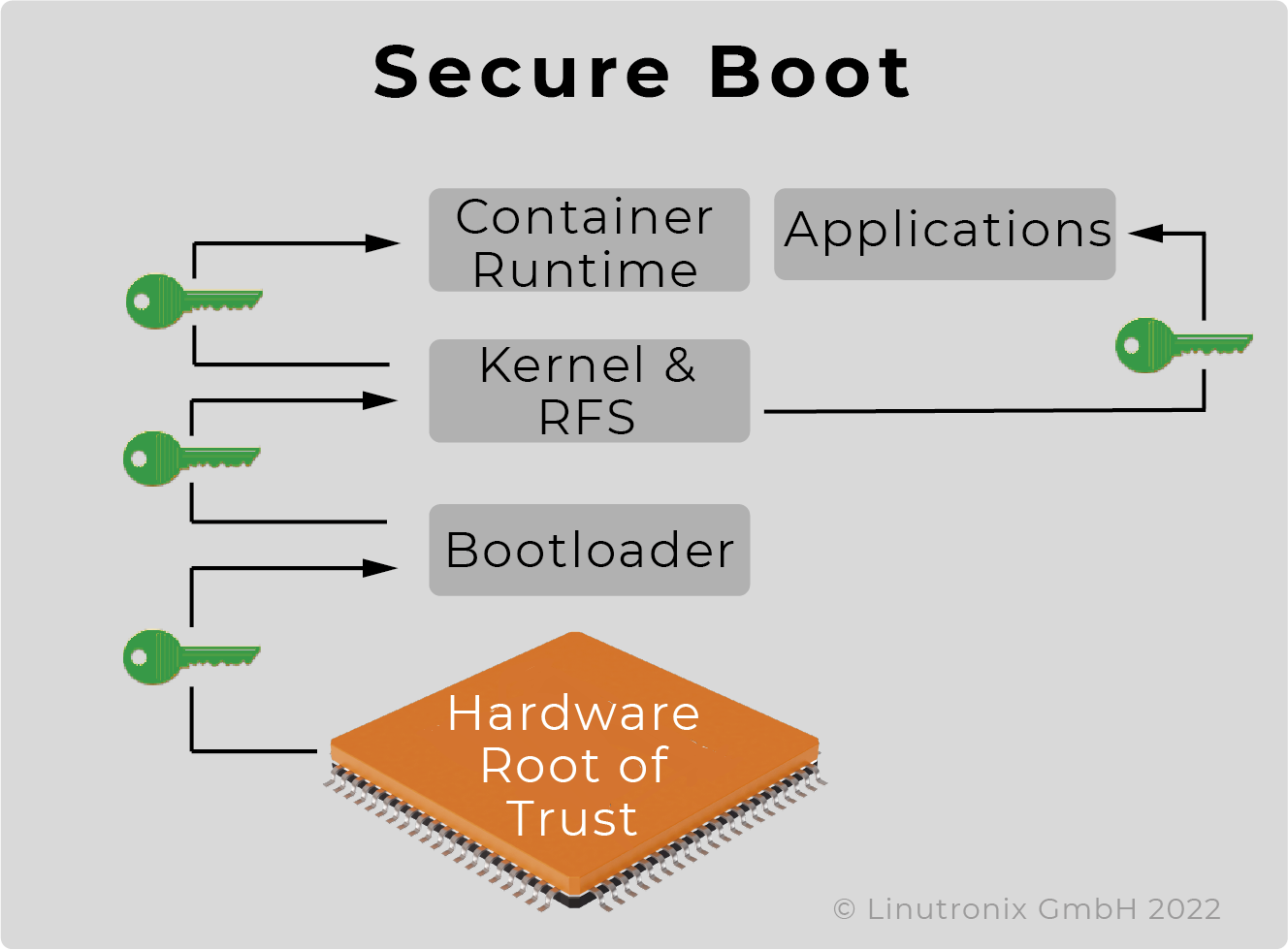
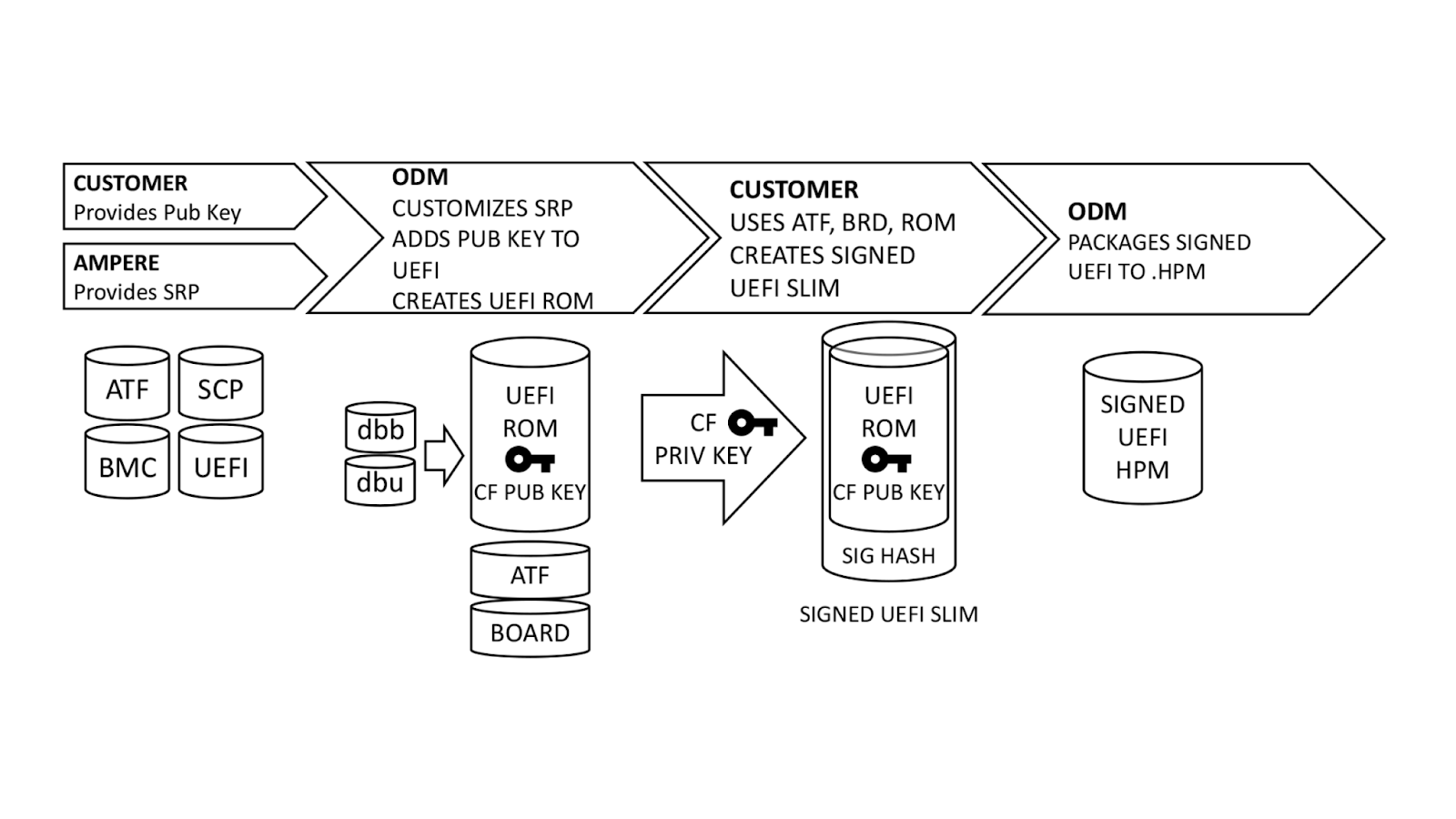
Secure Boot on ARM systems – Building a complete Chain of Trust upon existing industry standards using

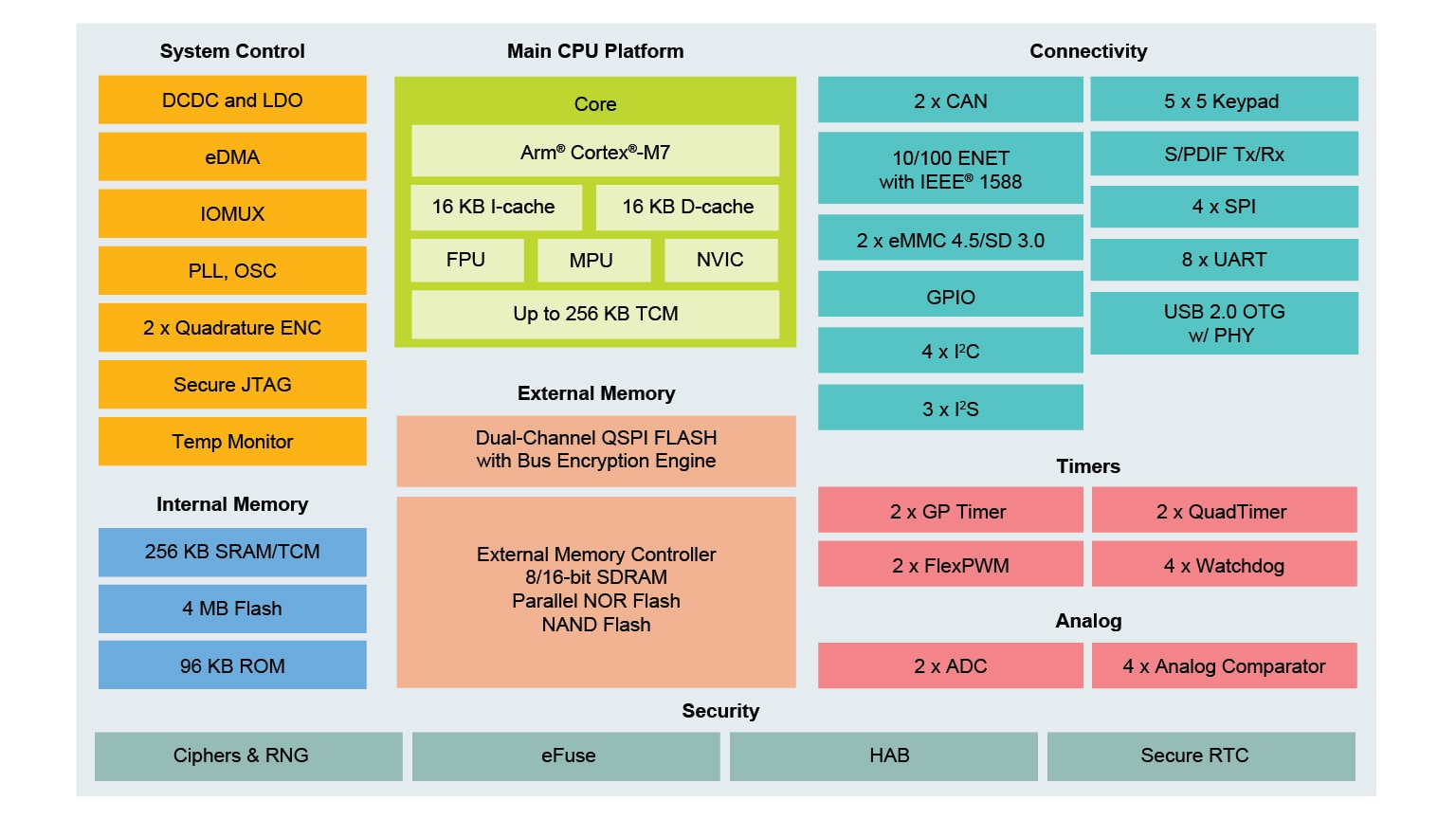
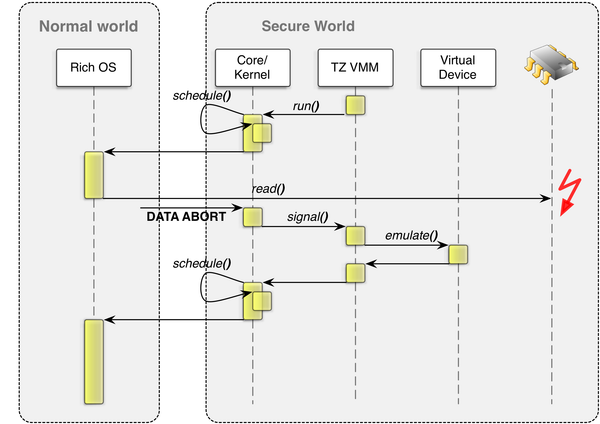
Designing secure embedded IoT devices - Architectures and Processors blog - Arm Community blogs - Arm Community
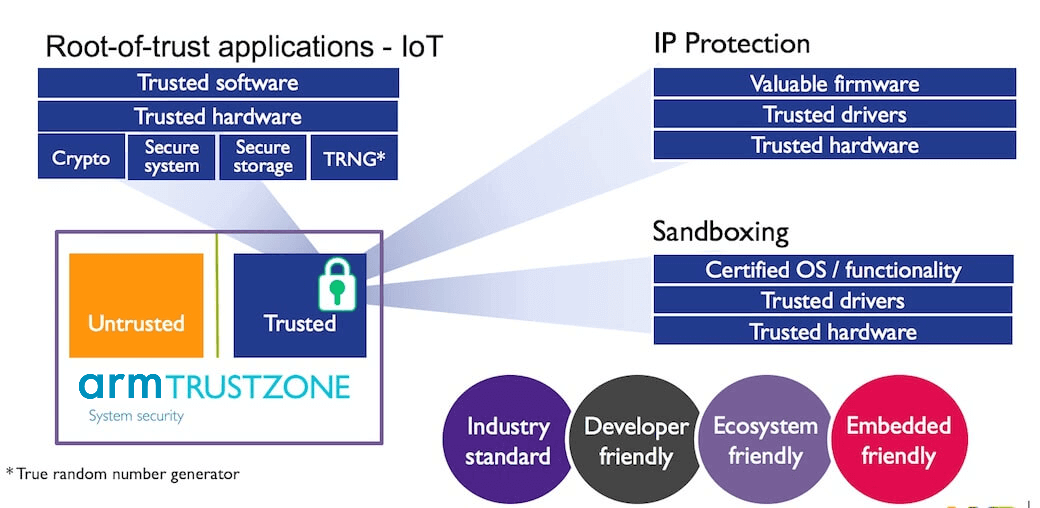
Designing secure embedded IoT devices - Architectures and Processors blog - Arm Community blogs - Arm Community

Linaro - Secure Boot on ARM Systems – Building a complete Chain of Trust upon existing industry standards using open-source firmware Check out how you can achieve this goal on ARM systems

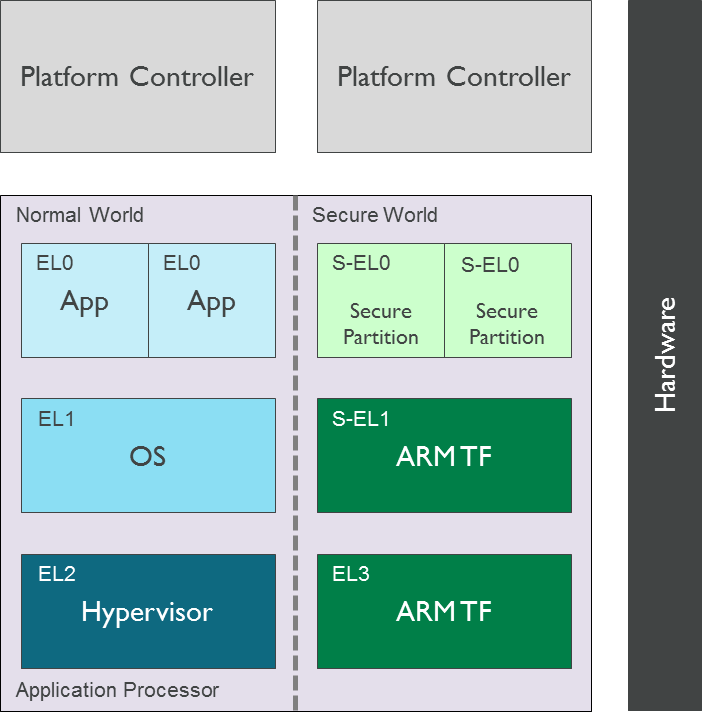
Linaro on Twitter: "If you want to learn more about Trusted Firmware M - an open source implementation of Platform Security Architecture(PSA) for ARM M profile processors. Click here https://t.co/k0FsFZqGVF #Linaro #Connect #