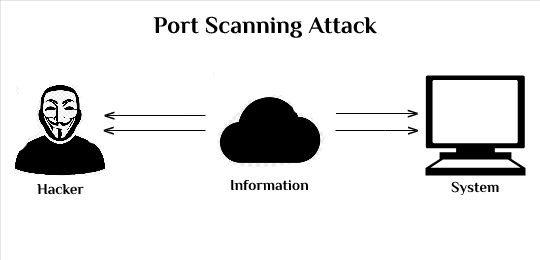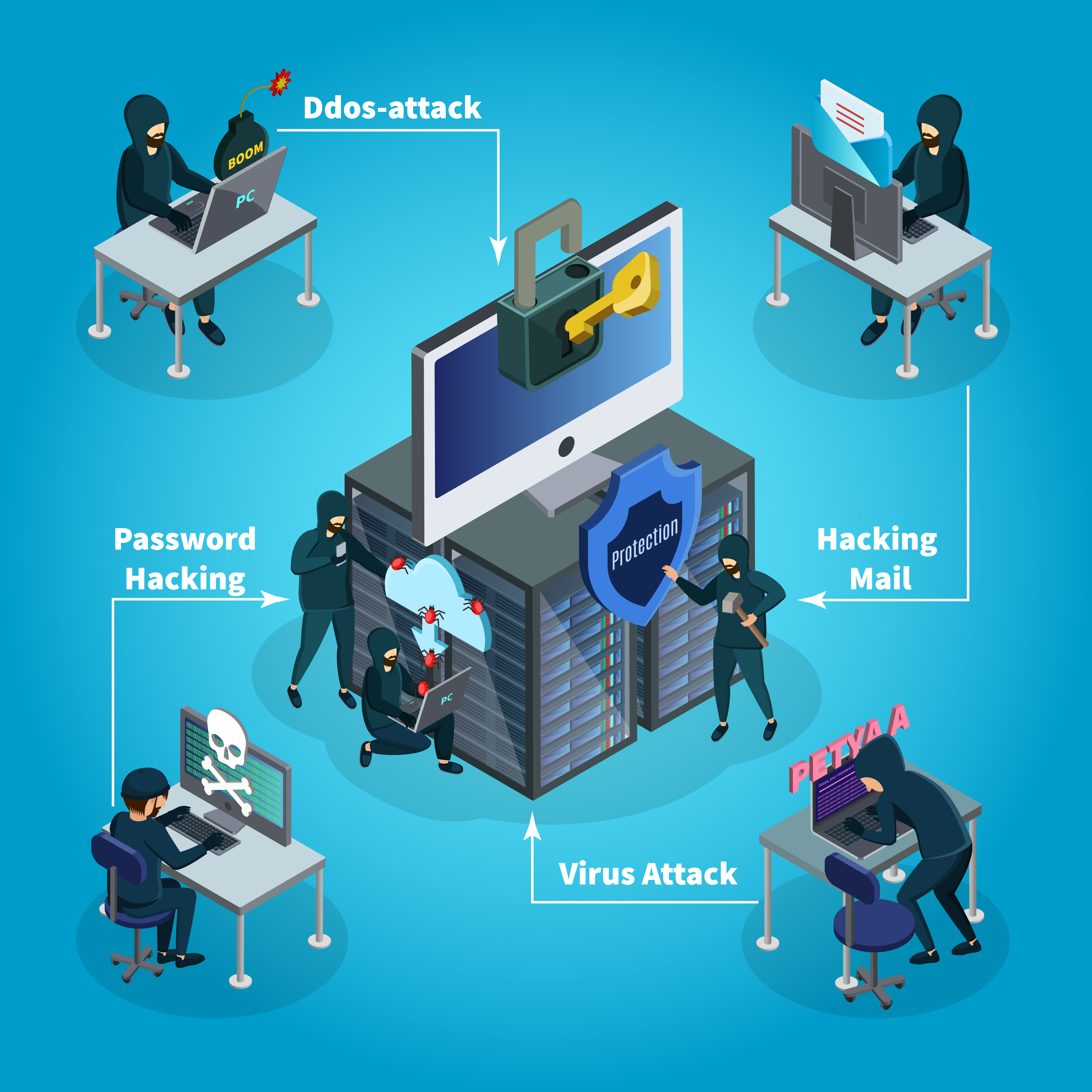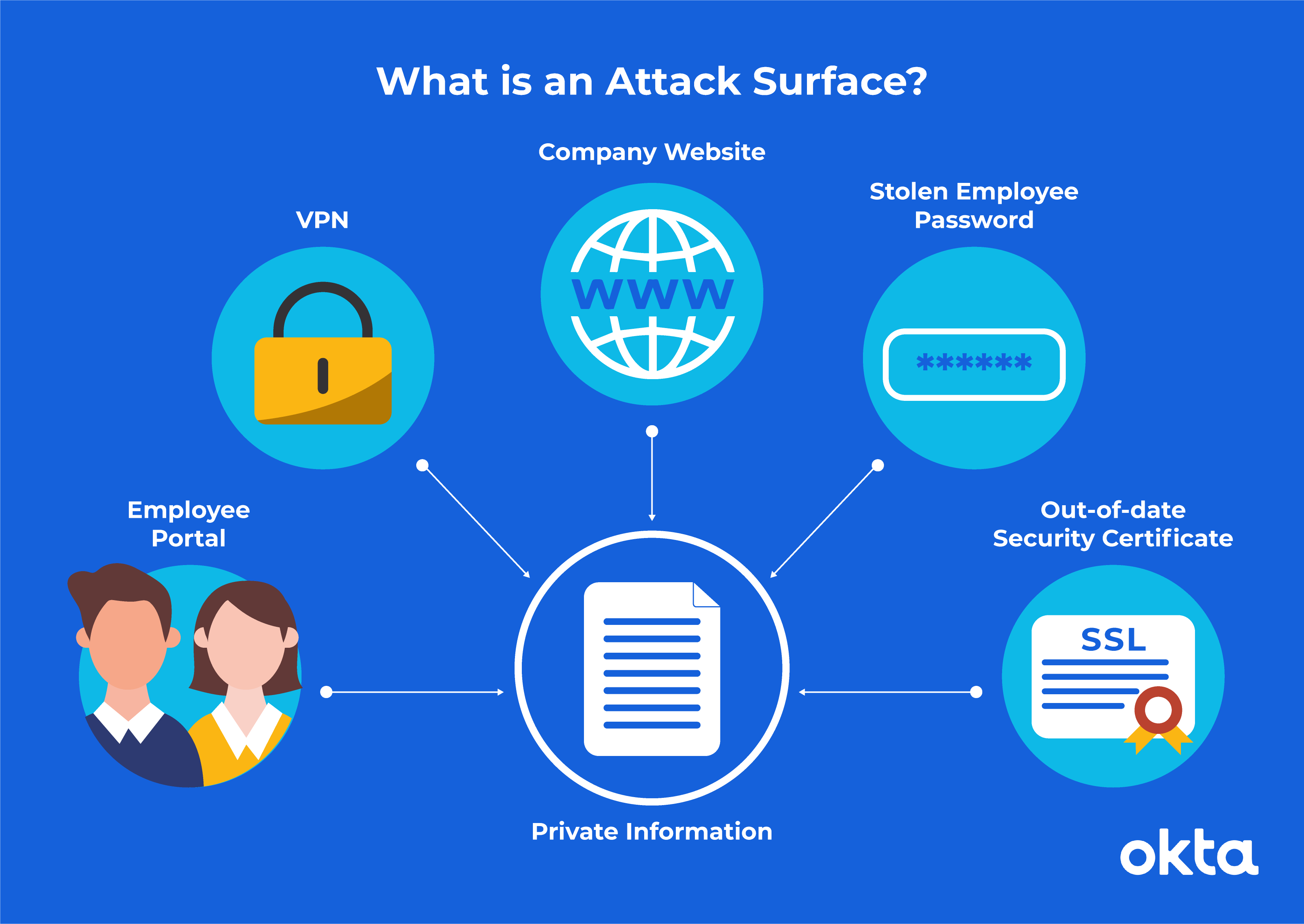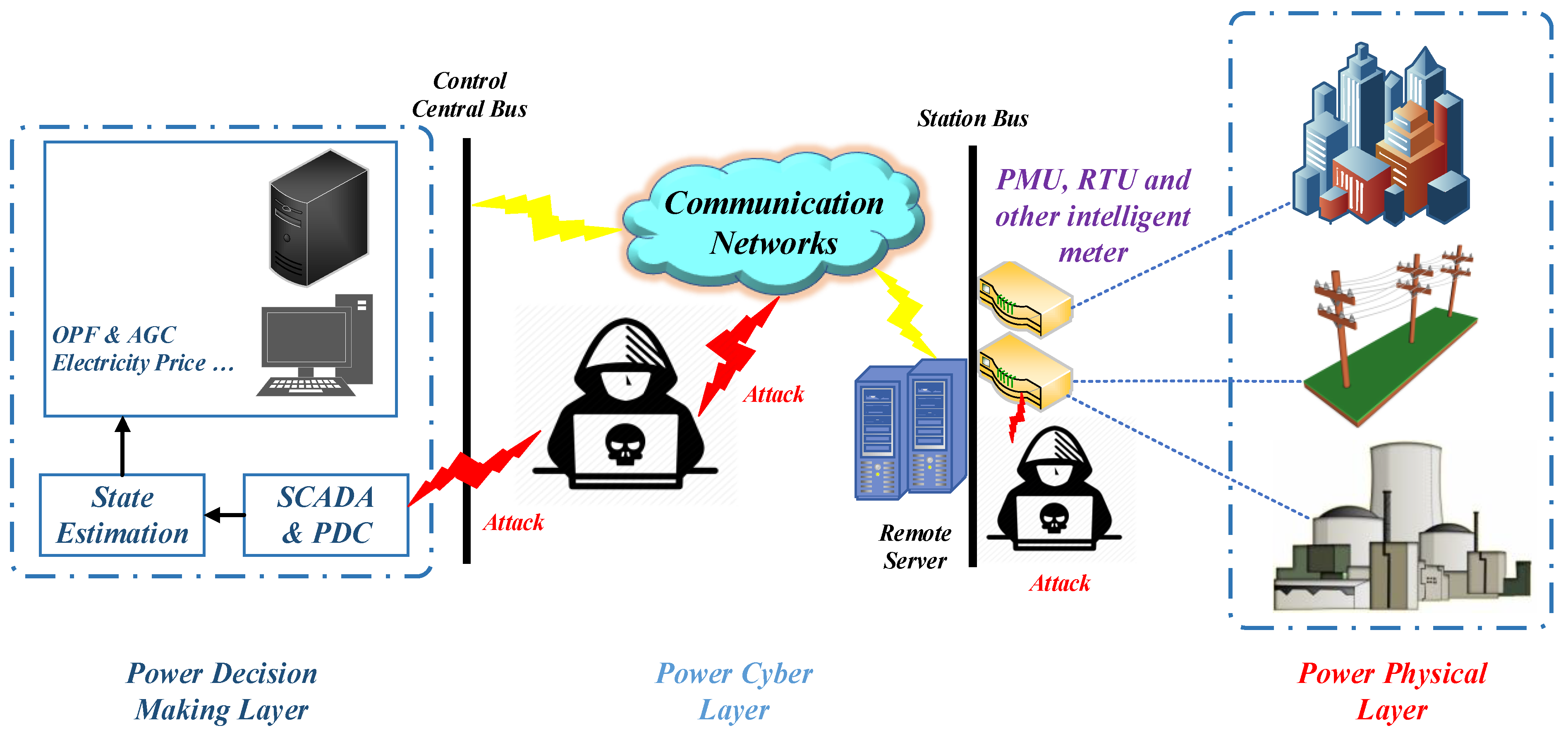
Mathematics | Free Full-Text | Deep Machine Learning Model-Based Cyber- Attacks Detection in Smart Power Systems

It could be taken down by an enthusiastic child': Whitehall wide open to cyber-attack, warn campaigners | Cybercrime | The Guardian

Vecteur Stock Protection from virus attack. Global antivirus secure system. Abstract blue background with various technology elements. Futuristic padlock vector illustration. Cyber attack protection. | Adobe Stock

Cyber attack, system breaking and malware. Faceless hooded anonymous computer hacker. Hacking and malware concept. Faceless man in hoodie with laptop in the dark Photos | Adobe Stock

Philadelphia Inquirer Operations Severely Disrupted by Cyber Attack, Offices Closed for Remediation - CPO Magazine