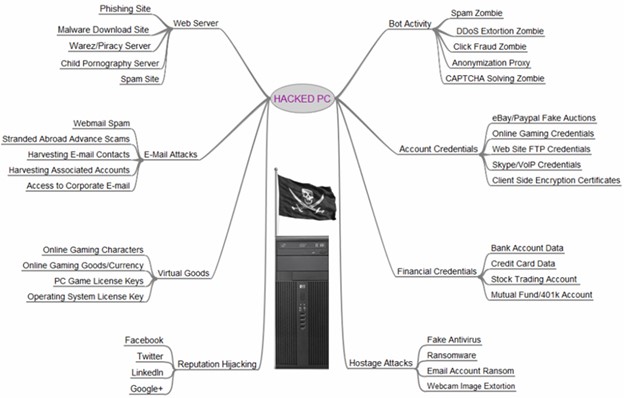
Chain of Supply Chain Attacks as 3CX Was Compromised by Outdated Futures Trading Software - CPO Magazine

Security breach, system hacked alert with red broken padlock icon showing unsecure data under cyberattack, vulnerable access, compromised password, virus infection, internet network with binary code - Review of Optometric Business

System hacked alert after cyber attack on taplet network. compromised information concept. internet virus cyber security and cybercrime.. Photos | Adobe Stock

Philadelphia Inquirer Operations Severely Disrupted by Cyber Attack, Offices Closed for Remediation - CPO Magazine